General Meeting November 15th, 2023
Presenter: Forta
Meeting Topic: Planning for the Future State of Data Protection.
IT organizations today face three main challenges: migrating to the cloud, getting the most out of their cloud investment, and protecting their investment against threats of ransomware and downtime.
Flexential and Fortra’s Alert Logic discussed the important components of managing both while meeting today’s budget challenges and organizational security requirements around data protection, detection and response.
.
General Meeting June 7th, 2023
Presenter: Proofpoint, ePlus
Meeting Topic: Threat landscape update with an emphasis on MFA evasion risk.
General Meeting March 8th, 2023
Presenter: Check Point
Meeting Topic: Check Point MDR specialists, with the assistance of Check Point field security engineering discussed the multitude of thoughts and ideas customers must consider when:
- Building out their own fully functioning 7×24 security operations
- Hiring out their “entire” security operations
- Hiring a security operation service to fill their current security operations gap a client might have
General Meeting January 11th, 2023
Presenter: Palo Alto Networks
Meeting Topic: Securing the Journey to the Cloud
Cloud applications are at the heart of digital transformation. With their scalability, ease of operationalization, and better resource utilization, it’s no wonder why researchers and IT departments are turning to the cloud. With all of the benefits of cloud computing come challenges and risks so it is critical to be able to secure the crown jewel, your data.
Learned how you can ensure security and privacy of your organization’s cloud computing efforts using the cloud smart strategy and leveraging the low hanging fruit of cybersecurity best practices.
This session demystified the cloud, paint the picture of the cloud journey, and armed attendees with best practices and strategies to secure your organization’s most sensitive assets and data in the cloud.
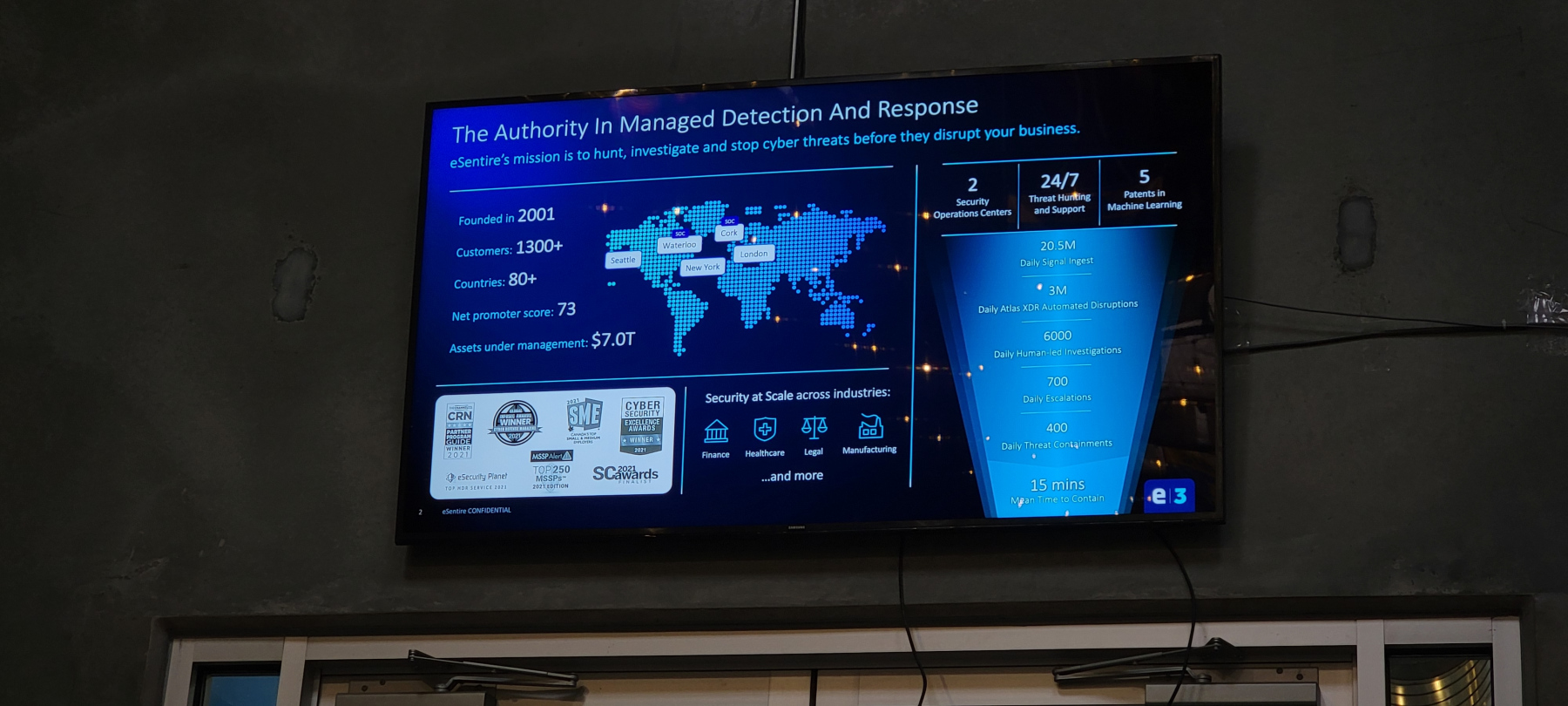
General Meeting September 14th, 2022
Presenter: eSentire
Meeting Topic: Demystifying MDR
In this presentation, Mike Sci, Senior Solutions Architect for eSentire, provided insight on how cybersecurity is really a big data problem and show you how to be an educated consumer of MDR (Managed Detection and Response) and managed security solutions. We learned to evaluate and define MDR solutions to separate fact from fiction in a rapidly growing security segment. He showed us how eSentire MDR provides full spectrum visibility, sorting through the tsunami of data, providing real time detection and embedded incident response.
General Meeting June 22, 2022
Presenter: Red Canary
Speaker Bio: Eleysia Friend (Customer Solutions Engineer with Red Canary ) has lived in many places throughout the years but currently lives in Las Vegas, Nevada. She is a recent addition to Red Canary and brings with her solid experience in Incident Detection and Response as well as Enterprise Security Operations. Outside of work Eleysia enjoys hiking, river floating, kayaking, great food and travel.
Ransomware has been a dominant cybersecurity threat for the better part of the last decade. However, it doesn’t walk alone. It’s almost always the eventual payload delivered by earlier-stage malicious software or activity. Luckily, if you can detect the threats that deliver the ransomware, you can stop the ransomware before it arrives.
In this talk, we’ll extensively reference Red Canary’s 2022 Threat Detection Report, examining the malware and other malicious tools that adversaries often use to deliver ransomware. While the specific trojans and strains of ransomware may change from one attack to the next, adversary tactics, techniques, and procedures are often similar across campaigns and threats. By developing robust detection coverage for the techniques adversaries abuse most often, rather than focusing on individual threats, security teams can achieve defense-in-depth against the many threats that leverage those techniques and the broader trends that dominate the infosec landscape.
Want to learn more about the prevalent adversary techniques and threats that can lead to a ransomware infection? Attendees will leave with:
- A better understanding of the threats and tools that commonly precede a ransomware infection
- Guidance on relevant collection and data sources that offer visibility into the threats and techniques that adversaries use to deliver ransomware
- Actionable information on how security teams can develop the capacity to detect, prevent, and mitigate ransomware and other threats
- Strategies for testing their ability to observe and detect common threats with free and easy-to-use tools like Atomic Red Team
If you would like to learn more about Red Canary’s 2022 Threat Detection Report, check it out here.
General Meeting April 13th, 2022
Presenter: Grip Security
Ken Granger discussed how the current SaaS Landscape is causing blind spots and unchecked risk, and innovative approaches that can help.
Speaker Bio: Ken Granger, Director of Solution Engineering, US West
General Meeting December 1st, 2021
Presenter: Palo Alto
Zero Trust experts explained the critical connection between Zero Trust and identity best practices and speeding your Zero Trust journey. A Zero Trust approach to network security is critical for safeguarding productivity in this new era of accelerated digital transformation, expanded hybrid work, and increased migration of apps and data to the cloud.
What we covered:
- What it means to be a Zero Trust enterprise
- How identity is foundational to a Zero Trust approach
- How to integrate strong identity best practices to fuel your Zero Trust journey
General Meeting June 2nd, 2021
Presenter: iPRESIDIUM
- The Current Threat Landscape and the Risks Organizations Face
- Discuss Proactive Threat Hunting on an organization’s endpoints
- Best practices/Framework
General Meeting March 3rd, 2021
Presenter: Sophos
Cyber Security Threats and Sophos MTR
General Meeting January 22, 2021
Presenter: Palo Alto Networks
Palo Alto Networks Presents: Crypsis Overview
The Ultimate Test Drive where we got hands-on experience with Palo Alto Networks Cloud-Delivered Security Services. In this free workshop we learned the value of preventing and detecting unknown malware, zero-day exploits, APTs, and other advanced cyber attacks and how to tie them to specific users and devices so they can be stopped efficiently.
We also learned how to:
- Go beyond traditional IPS to prevent all known threats across all traffic in a single pass
- Modern malware protection with ML-powered Analysis
- Use predictive analytics to disrupt attacks that use DNS
- Enable safe access to the internet for users in any location by preventing known and new malicious websites
- Rapidly identify and protect all unmanaged IoT and OT devices with a machine-learning-based, signature-less approach
General Meeting September 30th, 2020
Presenter: Crowdstrike
It’s clear that cyber crime and cyber criminals are not abating during the global upheaval caused by COVID-19. We recognize that remote work is still the norm for many organizations, especially as some states loosen/tighten restrictions. This situation begs important questions: Is your organization prepared to detect, respond and recover from a cyber incident during this time? Has the move to remote working negatively impacted your security operations and your ability to protect your customers, employees, and environment?
In this session, we learned:
- How the team gains visibility into endpoints and is able to contain systems outside the corporate network
- The advantages of using Real Time Response to remotely remove malware without the need to rebuild systems
- How you can recover your environment from advanced threats and attacks and establish a maximized security posture
General Meeting June 3rd, 2020
Presenter: Juniper – Dwann Hall and Jeff Bird
Today’s rapidly evolving threat landscape is outpacing the efficiency of many current security solutions. Currently, about 80% of all Web traffic is encrypted. Without any insight into what the encrypted Web traffic is doing, it leaves a major attack vector for criminals to exploit your network. New Zero-Day malware variants are launched every day. NGFW features & Anti-Virus Signatures cannot see threats hidden in https encrypted Web traffic. Attacks are more prevalent in encrypted Web traffic these days. Encrypted Web traffic attacks can affect your business at any moment in time.
General Meeting March 4th, 2020
Presenter: Mike Neary
Special Speakers: Local FBI Agent